By 'jailing' the 'germ' within the limits of a given host, Jail Host prevents it from spreading out to the rest of the account,offering extra protection against intruders who have managed to infiltrate
into the system
Now the Jail Host option is enabled by default for all newly created hosts to double protect them from intruders.
How does the Jail Host option work?
The main purpose of Jail Host is to
outsmart eventual intruders.
Even though security solutions are
getting more and more reliable, hackers seem to always be one step ahead of the game. The truth is that no universal painkiller for hack attacks has been invented yet.
This is where the extra Jail Host barrier can come in real handy.
If an intruder does manage to break into a website, if Jail Host is enabled, they will not be able to move to another host and spread their malicious activity.
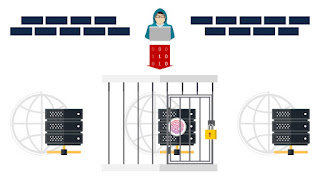
Here is an illustration of how the Jail Host feature basically works:
As you can see in the figure above, the Jail Host-enabled domain is practically isolated from the other hosts in the /www directory within the same hosting account.
This prevents intruders from using the host as a doorway to the rest of the system in the event of an attack.
The tight encapsulation works at the Operating System level, which
guarantees its efficiency in all possible hacking scenarios.
By ensuring a segmental level of
protection, the Jail Host feature offers an innovative approach to keeping a hosting environment clean of smart intruders.
This way, even if one of your hosts
succumbs to an attack, you will have the rest of your content fully intact.
What will happen to already added hosts?
If you already manage domains with us,you can enable 'jail host' protection for them from the Hosted Domains section of the Web Hosting Control Panel.
In the Actions column of the table of
hosted domains, search for the Edit host option:
You will find the Jail host option at the bottom of the Edit host form:
Just tick the box and click on the Edit Host button to complete the action.
The Jail host functionality is supported on all web hosting services, which are compatible with the Hepsia Control Panel including cloud hosting packages,
Virtual Private Servers, semi-dedicated servers and dedicated servers.
http://www.josidelhosting.com
www.josiahdele.blogspot.com
Comments