 here's the best way to profit from hacking On Wednesday, police around the world coordinated an incredible bust, closing down a enormous, highly-guarded black market for hackers.
here's the best way to profit from hacking On Wednesday, police around the world coordinated an incredible bust, closing down a enormous, highly-guarded black market for hackers. Darkode, the shuttered black market, was a domain the place hackers would change their dangerous wares.
Criminals would swap large batches of stolen statistics. identity thieves would purchase databases of Social security numbers and credit score cards. Cyberweapons dealers would promote malware that might ruin into executive and company desktop networks -- or fry hardware and trigger hundreds of thousands of greenbacks in damage.
Hackers who snuck into thousands and thousands of computers -- and turned them right into a slave network below their manage -- would promote brief entry to their potent computing energy of their "botnets." These are continually used to attack web sites, overloading them and knocking them offline.
David J. Hickton, a federal prosecutor in Pennsylvania who helped lead the attack, referred to as Darkode "one of the gravest threats to the integrity of statistics on computers in the united states and all over the world."
The U.S. Justice department estimate there are virtually 800 crook cyber web forums global. Hickton described Darkode as "the most subtle English-speaking forum for criminal computing device hackers on the earth."
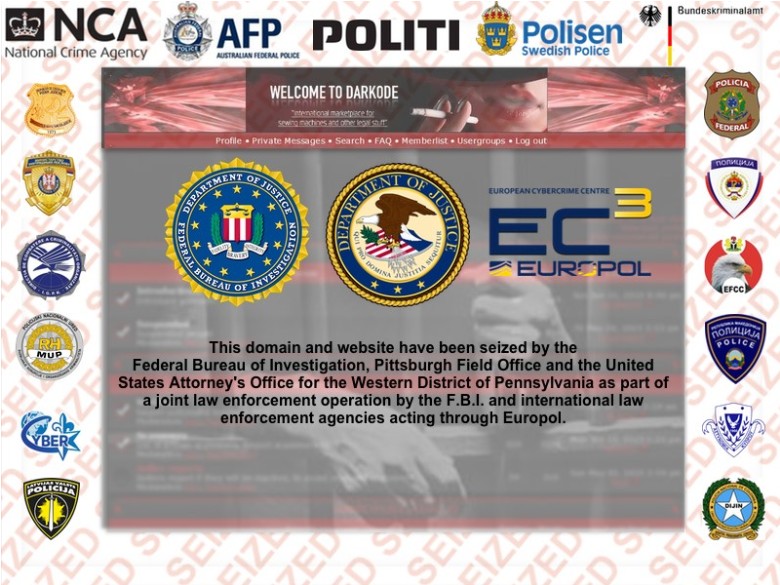 here is what the hacker black market Darkode appears like now.
here is what the hacker black market Darkode appears like now. As a part of "Operation Shrouded Horizon," FBI brokers went undercover, infiltrating Darkode with the assist of police in Australia, Brazil, Colombia, Finland, Germany, Nigeria and a couple of other nations. Federal officers known as the operation "the largest coordinated international legislation enforcement effort ever directed at an online cyber-crook forum."
And now the Justice depa rtment goes after individual hackers too.
On Wednesday, it named 12 individuals suspected of taking half within the discussion board -- and most of them live within the u.s..
What makes this such a huge takedown? It was wickedly difficult to infiltrate this tight knit hacker circle.
essentially the most unhealthy and legitimate black market hacker forums have tightly closed doorways. it's an exclusive membership included through passwords. A strict vetting system maintains out police officers and researchers. You ought to deliver proof of genuine hacks to profit credibility -- and the extra credibility you have got, the nearer that you can entry the complete market.
however the FBI managed to sneak in anyway.
 Hackers steal statistics from federal organizations
Hackers steal statistics from federal organizations related: Hackers stole 1.1 million fingerprints from the federal govt
related: commonplace Android online game stole fb logins
related: This business sells undercover agent equipment to evil governments < /p>
Comments